Although Rogue antivirus business is very profitable for cyber criminals, it has one weak point – payment processing. Basically, one needs a legitimate partner to do this, or one would have no way to get the money from credit cards except by using the cards to buy some goods (which is more dangerous). Additionally, other limitations exists – the overall charge back ratio should be low (around 3% if memory serves me right) or the Visa will close the ability to get money.
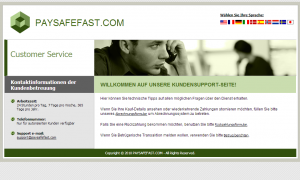
One of the payment pages used for Rogue antiviruses
Thus the temporally closure of Chronopay was a significant hit to rogue antivirus makers. They had enough legitimate clients to keep charge back ratio low, and rogue business stopped for almost a year. Although it had returned, the lack of payment processor forced the makers to look into some other options to make money. Also, other payment processors started doing their business by using banks in various countries.
Today, security researcher Xylitol posted about Black Processor, one of the payment processors accepting fake antiviruses that uses Lithuanian banks. It looks like (according to screenshots) that the bank well knows participating in illegal payment collection. This worries me a lot, as we had a problem with one of the banks already. Being abused by criminals is one thing, cooperating with them is completely other.
Although it is not clear which bank helps malware makers, there are little of them in Lithuania. Full list of Lithuanian banks is here : http://lb.lt/banks , although, I think some
other institutions would be possible too, even if they used the word “bank”: http://lb.lt/credit_and_payment_institutions . The list could be simplified further if one removes foreign-capital banks from the list ( I do not thing that Scandinavian banks subsidiaries would risk their reputation).

0 Comments