WordPress powers more than a half of sites having some sort of CMS. Thus it is not surprising that these websites come under automated attacks and get infected sometimes. So, what to do? Well, that depends on type of attack used and its results. Some possible ways of site to get hacked are listed below:
Table of Contents
FTP or Shell credentials got compromised
This type of attack can be detected by checking login logs for server access and is available from administration panel of your hosting provider usually. Sometimes they originate from your IP. In such cases, your PC is infected too.
The worst kind of infections are when server administrative users are infected. In some cases this is due to software vulnerabilities, but you should change your login information after the clean up too.
Typically, such hacks are used to use server for sending spam, defacements or as proxy for other attacks. The best way to secure from password leackage is using long, complex passwords and using sftp /ssh access when possible. Never use FTP access, as it sends login data without encryption.
Software vulnerabilities
Another way to get serious infection is web server or FTP server bugs that allow execution of downloaded code. For cleaning this up, you will have both upgrade your software and remove downloaded malware.
Typically, Web server user has access to most of the data on server. Thus even if hackers can’t log in themselves, they can do lots of things with your websites and infect them.
Brute Force attacks for wordpress users
Most of wordpress skins provide lots of information about users having access to the admin panel. Firstly, there is admin user in most of the cases. Secondly, each of the user have author pages with their login names in page url. Thus getting login names is easy. It is not so easy to recover their passwords.
WordPress passwords can be recovered using brute force attacks, aka posting various password guesses automatically to the login form. If the user uses simple passwords, they might be guessed.
Once inside, hacker can edit all your posts and add link to a malicious site or the one they wish to promote. If admin account is compromised, hacker can edit whole site too.
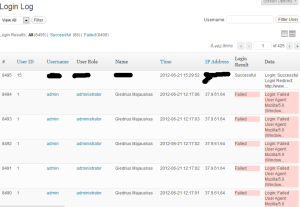
There are ways to prevent such attacks, for example limiting IP address for WordPress panel, moving it around or special security plug-ins. One usefull plug-in is Simple Login Log, which would show you failed and successful login attempts.
Additionally, you should be cautious about people brute-forcing your phpMySql install and shell account password.
WordPress theme and plugin vulnerabilities
Lots of wordpress infections happen due to wordpress plug-ins. Some of the plug-ins are were coded without any security precautions. This is especially true for ones that work with uploaded content like images or media. It is not surprising that TimThumb was used for infecting WordPress for a while, though other plugins are used too.
Thus it is critical to limit Plugin count to the minimum required for site to operate, and keep them up to date.


2 Comments
fontanalorenzo · June 28, 2012 at 6:45 pm
Pay attention a lot of to WordPress plugins, if you are using one of these (link) you are vulnerable to hackers attacks..
http://fontanalorenzo.it/wordpress/security/50-wordpress-plugins-vunlerable-to-arbitrary-file-upload.html
How to fix hacked Wordpress site? — Giedrius Majauskas blog · June 30, 2012 at 1:46 pm
[…] Time to open your site and determine HOW and WHY your site got infected. There are several possible scenarios, that are covered in a dedicated post about ways WordPress get hacked. […]